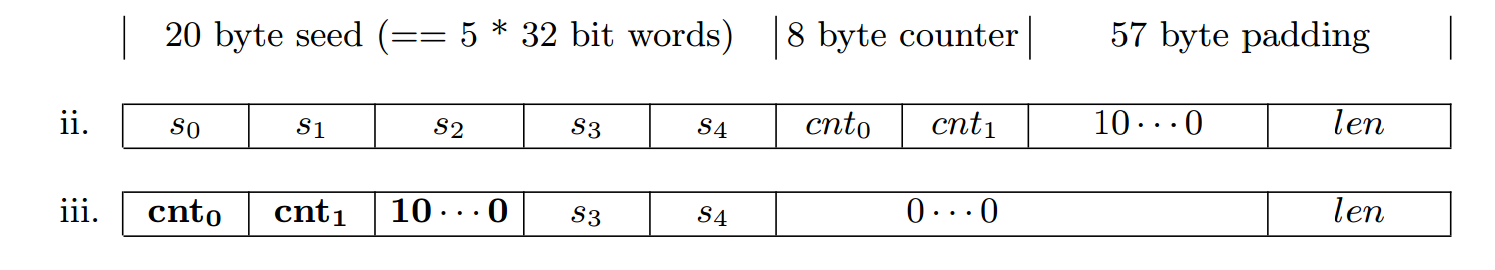
下面这张图可以形象的表述这个过程:
Google已经发布了patch。看下Diff文件:
hxxps://android.googlesource.com/platform/libcore/+/ab6d7714b47c04cc4bd812b32e6a6370181a06e4%5E%21/#F0
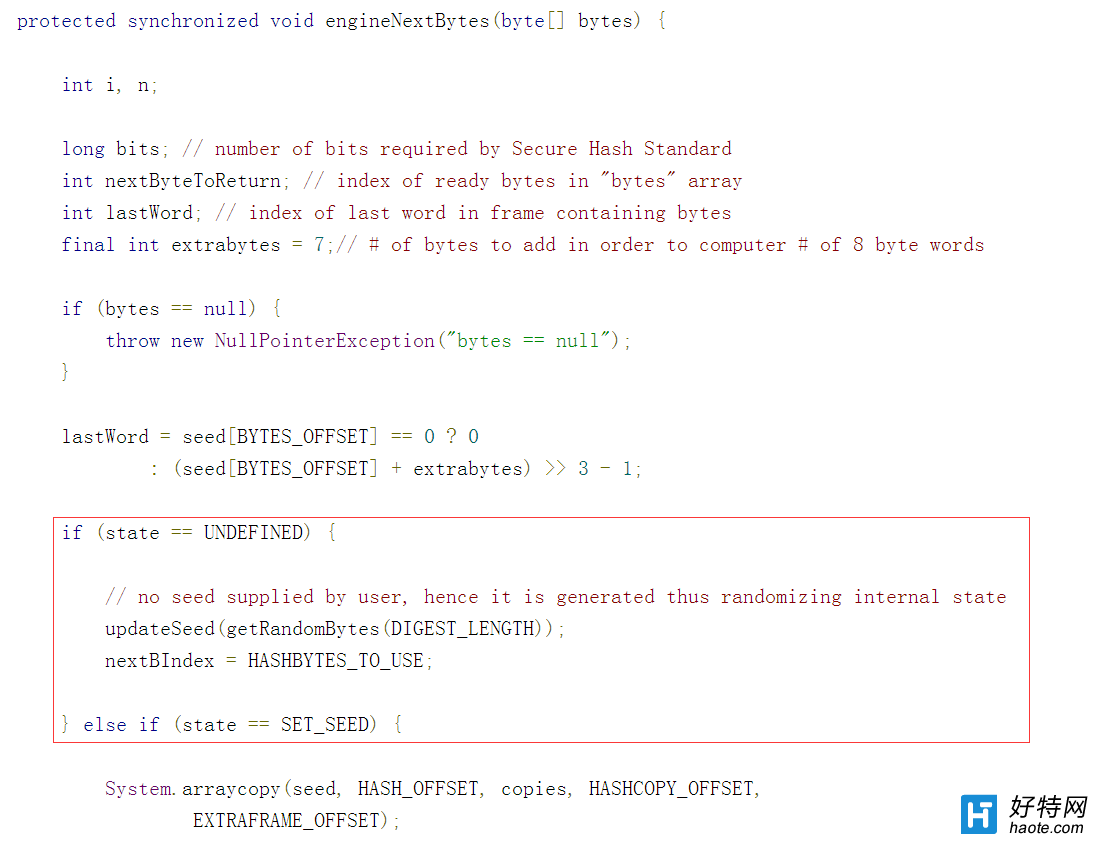
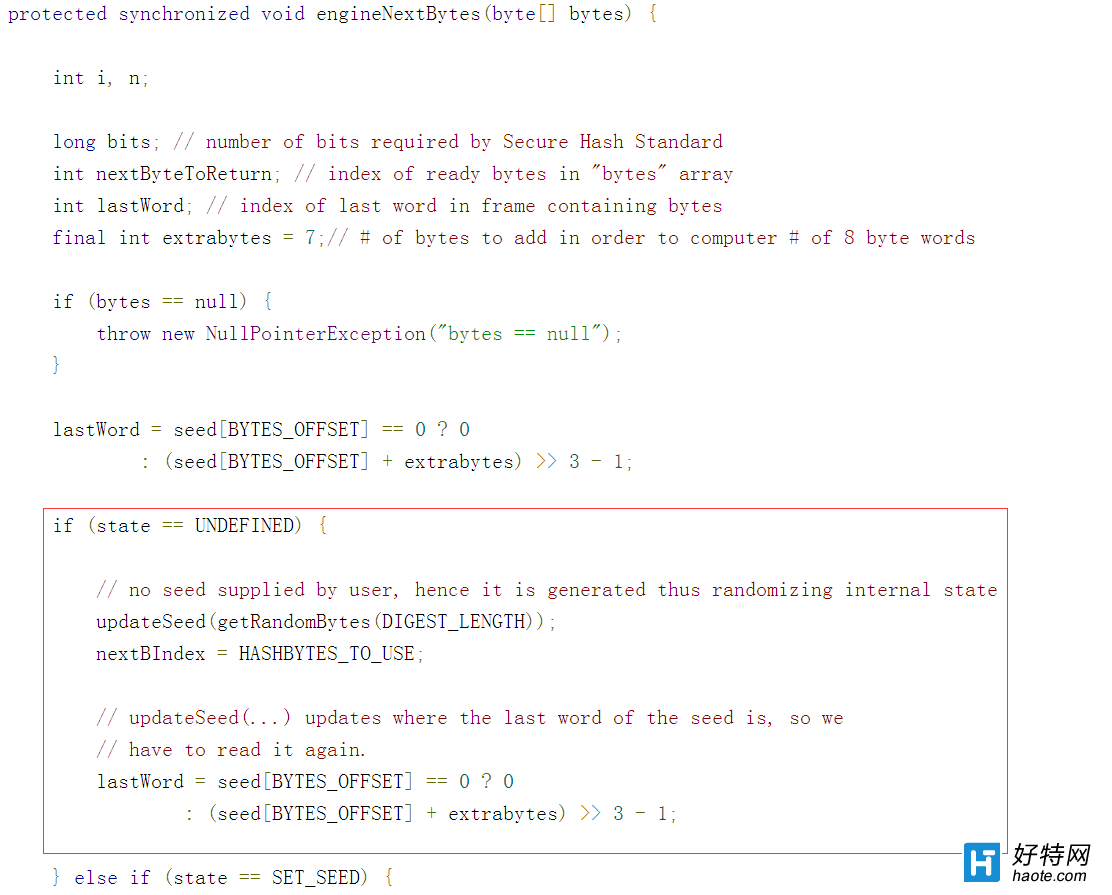
发现fix文件里在调用完updateSeed函数更新之后,重新读了下seed 的last word。
对于普通开发者来讲,可以使用下面链接中的方式进行修复。
hxxp://android-developers.blogspot.com.au/2013/08/some-securerandom-thoughts.html
(1)hxxps://android.googlesource.com/platform/libcore/+/kitkat-release/luni/src/main/java/org/apache/harmony/security/provider/crypto/SHA1PRNG_SecureRandomImpl.java
(2)hxxp://resources.infosecinstitute.com/random-number-generation-java/
(3)hxxp://developer.android.com/reference/java/security/SecureRandomSpi.html
(4)hxxp://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-7372
(5)hxxp://android-developers.blogspot.com.au/2013/08/some-securerandom-thoughts.html
小编推荐阅读